What is AppSOC?
AppSOC is an application security platform that consolidates findings from multiple security scanners, prioritizing vulnerabilities based on business impact and exploitability. It helps security teams reduce alert overload by up to 95% and improve response times, allowing them to focus on addressing critical risks in their software development lifecycle.
What sets AppSOC apart?
AppSOC stands out with its AI-driven security prioritization, which helps security teams and DevOps professionals focus on the most critical vulnerabilities. This approach improves collaboration between teams by providing a shared understanding of security risks. AppSOC's unique method of contextualizing threats allows organizations to align their security efforts with business objectives.
AppSOC Use Cases
- AI security governance
- Application vulnerability management
- Risk-based prioritization
- Security posture monitoring
Who uses AppSOC?
Features and Benefits
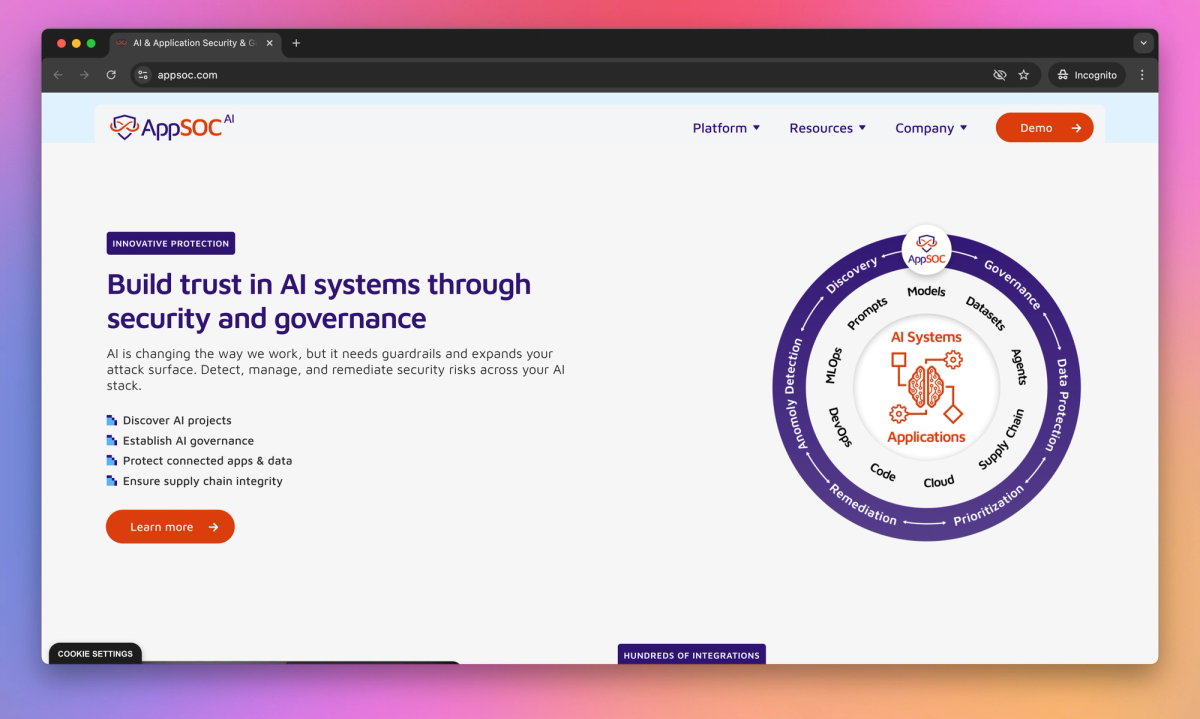
- Safeguard AI systems with comprehensive protection, including discovery of shadow AI, establishment of guardrails, and management of security for models, datasets, and MLOps.
AI Security & Governance
- Streamline AppSec by unifying management of security issues across various tools, including SAST, DAST, SCA, IaC, and cloud security.
Application Security Posture Management
- Prioritize security issues based on business context, ensure compliance through SLAs, and track security across the entire application lifecycle.
Code-to-Cloud Vulnerability Management
- Manage risks from libraries and third-party code while mapping security issues to your application hierarchy.
Supply Chain Risk Management
- Focus on critical vulnerabilities by evaluating severity, exploitability, and business impact to address the most pressing security risks first.
Risk-Based Prioritization
Pricing
Custom Price not available
AI discovery
AI governance
Security posture management
Runtime protection
Application security
Remediation
AppSOC Alternatives
Remove sensitive information from your documents
Safeguard your platform from online threats
Supercharge your SOC's threat response








