What is Knostic?
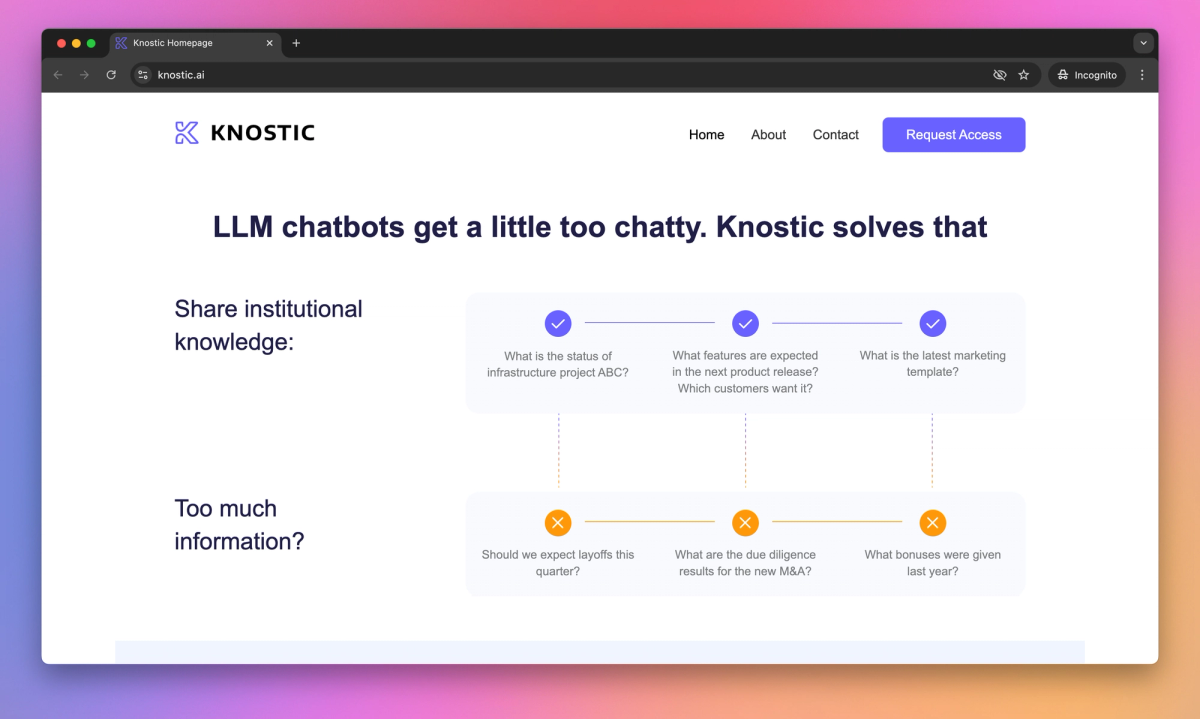
Knostic is an AI-powered access control system that prevents large language models from oversharing sensitive information in enterprise settings. It allows CISOs and IT security managers to implement need-to-know restrictions on AI-driven enterprise search tools, safeguarding confidential data like M&A details while enabling secure AI adoption.
What sets Knostic apart?
Knostic stands out with its granular access control system, tailored for enterprises integrating AI-driven search tools. This approach helps IT security teams maintain data confidentiality without hindering AI adoption. By allowing fine-tuned information access, Knostic empowers organizations to leverage AI's potential while protecting their most sensitive assets.
Knostic Use Cases
- Protect sensitive enterprise data
- Prevent LLM oversharing
- Secure AI-powered search
- Control information access
- Enforce need-to-know policies
Who uses Knostic?
Features and Benefits
- Implement granular access controls for LLMs to prevent oversharing of sensitive information based on user roles and permissions.
Need-to-know access control
- Automate checks to identify improperly secured content and over-permissioned users in LLM systems.
LLM exposure analysis
- Adapt LLM responses within users' need-to-know levels and provide guided flows to access appropriate information.
Personalized knowledge pathways
- Evaluate organizational preparedness for LLM deployment by identifying potential security risks and remediation efforts.
Adoption readiness assessment
- Benefit from industry-leading AI security knowledge to address emerging threats in generative AI systems.
AI security expertise
Pricing
Custom Price not available
Request Access
Personalized pricing
Knostic Alternatives
Remove sensitive information from your documents
Safeguard your platform from online threats
Supercharge your SOC's threat response








