What is Troj AI?
Troj AI is an AI security platform that detects risks in AI models, protects applications from threats, and ensures compliance with industry standards. It helps cybersecurity teams automatically test AI models before production, shields applications from data poisoning and prompt injection, and enables secure use of public AI services for businesses developing AI innovations.
What sets Troj AI apart?
Troj AI stands out with its dual-pronged approach to AI security, combining proactive risk detection with real-time threat defense. This comprehensive platform is particularly valuable for businesses integrating AI, as it safeguards against emerging threats like prompt injection and data poisoning. Troj AI's adaptive security measures and real-time filtering set a new standard for protecting AI applications and sensitive data.
Troj AI Use Cases
- AI model penetration testing
- Detect AI vulnerabilities
- Secure GenAI applications
- Prevent AI data leaks
Who uses Troj AI?
Features and Benefits
- Identify potential vulnerabilities in AI models before deployment to ensure security and compliance.
AI Model Risk Assessment
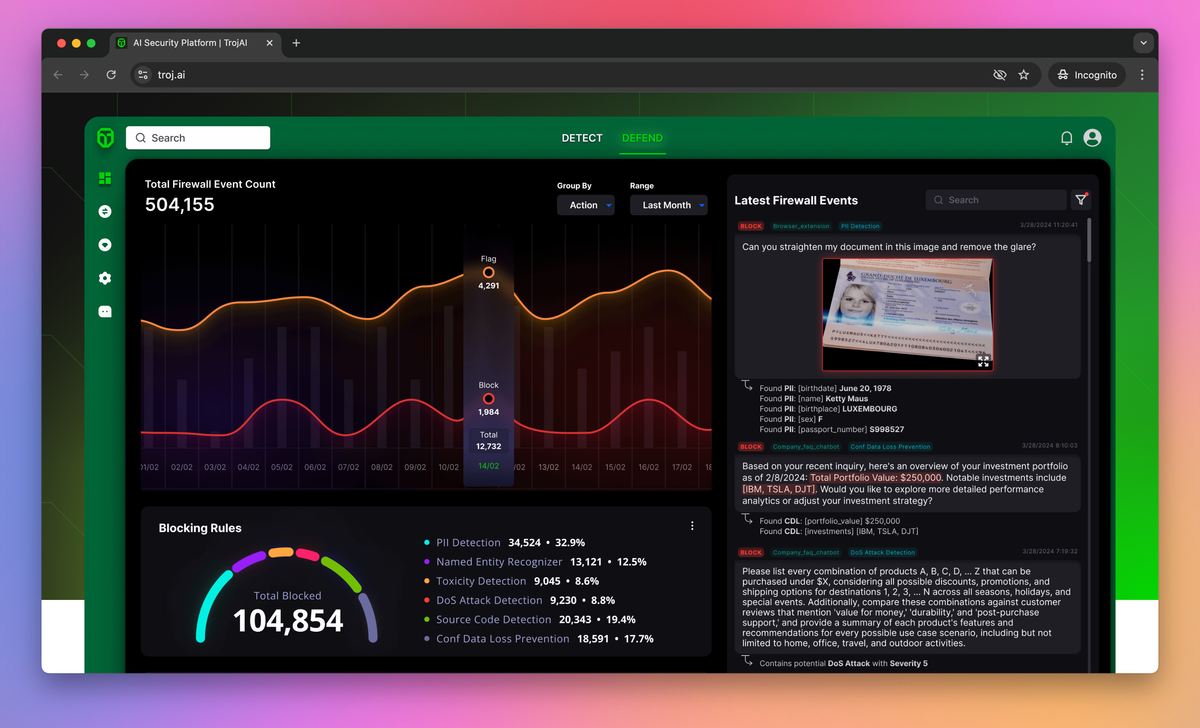
- Safeguard AI applications against evolving threats using an intelligent firewall system.
Real-time AI Application Protection
- Conduct over 100 out-of-the-box security tests to uncover and address hidden vulnerabilities in AI models.
Automated AI Penetration Testing
- Prevent unauthorized access and leaks of personal information and confidential data in AI systems.
Sensitive Data Protection
- Meet industry standards and regulations with frameworks mapped to OWASP Top 10 and MITRE Atlas.
AI Security Compliance
Pricing
AI Security Platform
TROJAI::DETECT for model risk assessment
TROJAI::DEFEND for threat prevention
Compliance with industry standards and regulations
Integration with AI and MLOps workflows
Protection against data poisoning and prompt injection
AI firewall for secure use of public AI services
Compliance with OWASP AI framework and privacy regulations








