What is Antimatter?
Antimatter is a data control platform that enforces permissions and anonymizes sensitive information in AI and data science applications. It allows security leaders to implement access control, classify data, and encrypt information, helping AI teams and data scientists use data responsibly while maintaining privacy and compliance.
What sets Antimatter apart?
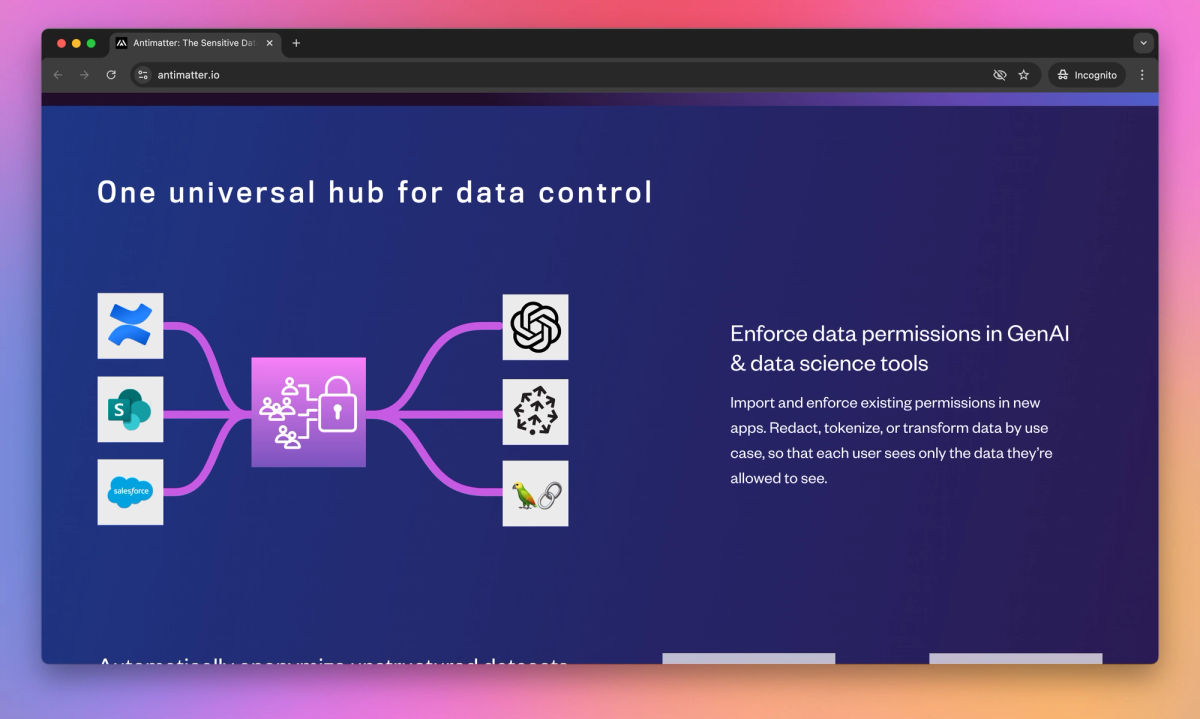
Antimatter sets itself apart with its data control plane, which enforces permissions across any data store or client application. This approach proves valuable for security teams looking to protect sensitive information in AI and data science workflows. By providing a universal hub for data control, Antimatter simplifies the process of implementing enterprise-grade security features, allowing companies to meet strict compliance requirements.
Antimatter Use Cases
- Enforce data permissions in AI tools
- Anonymize sensitive datasets
- Implement BYOK for enterprise customers
- Secure data for AI/ML applications
Who uses Antimatter?
Features and Benefits
- Enforce data permissions across GenAI and data science tools, ensuring each user sees only the data they're authorized to access.
Universal Data Control
- Detect and anonymize sensitive content in various data formats using AI-powered classification, with customizable redaction policies.
Automated Data Anonymization
- Control access to data regardless of storage location or access method, seamlessly integrating with existing permissions.
Access Control Integration
- Capture existing metadata and use AI classifiers to detect and tag sensitive information, providing a comprehensive manifest of protected data.
Data Classification and Inventory
- Secure data in encrypted capsules with options for native key management, bring your own key (BYOK), or hold your own key (HYOK) in an external KMS.
Flexible Encryption Options
Pricing
Access Control
Data Classification
Logging
Data Inventory
Data Anonymization / Transformation
Encryption








